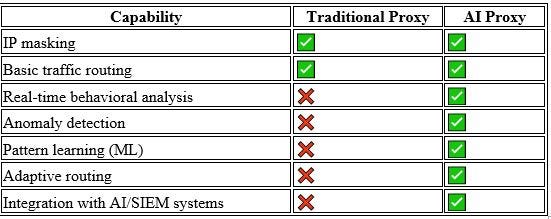
In the early internet era, a proxy was simply a middle-layer to mask IP addresses, bypass geo-blocks, or route traffic. But in today’s enterprise data environment, driven by AI and Big Data, the role of the proxy has fundamentally evolved.
It’s no longer a passive relay — it becomes an active control layer that can understand, learn, and protect data flow in real-time.
This gives rise to a new generation of proxies: AI Proxies, which differ drastically from traditional ones — especially when handling millions of requests and terabytes of data per day.

Under the pressure of high-volume data pipelines, traditional proxies begin to show cracks:
 Unable to distinguish malicious from legitimate traffic when the structure looks normal
Unable to distinguish malicious from legitimate traffic when the structure looks normal Lacks real-time traffic intelligence or adaptive control
Lacks real-time traffic intelligence or adaptive control Fails to detect stealth attacks like low-rate DDoS, impersonating bots, or data poisoning within legal payloads
Fails to detect stealth attacks like low-rate DDoS, impersonating bots, or data poisoning within legal payloads
61% of large-scale API attacks came through legitimate-looking traffic with subtle behavior anomalies — undetectable by static proxies.

AI Proxy is not just a smart pipe — it’s a real-time traffic brain that learns from behavior patterns and makes autonomous decisions:
 Analyzes traffic behavior and request patterns in real time
Analyzes traffic behavior and request patterns in real time Detects anomalies and flags potential threats proactively
Detects anomalies and flags potential threats proactively Auto-adjusts routing, rate limits, and access rules based on context
Auto-adjusts routing, rate limits, and access rules based on context
Before AI Proxy:
- API gateways hit 10M+ daily requests, causing frequent slowdowns.
- Attackers impersonated real user behavior, bypassing traditional proxy filters.
- AI detected subtle deviations in behavior (timing, frequency, header fingerprinting).
- System auto-flagged risky traffic and rerouted safely without interrupting legit flows.
- Problem: Crawled training data often contained noise, fake sources, or embedded bias.
- With AI Proxy: Traffic was analyzed and filtered in real time based on source credibility, behavior, and content similarity.
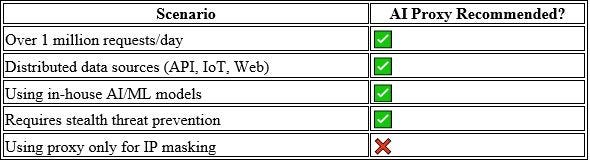
In a world where data is the lifeblood of enterprise growth, traffic control can’t rely on static routing or basic filtering.
You need a proxy that not only connects — but also understands.
AI Proxy doesn’t replace traditional proxy — it’s the mandatory evolution.
 Over 9 million IPs, with advanced geo-targeting
Over 9 million IPs, with advanced geo-targeting Real-time behavior monitoring and adaptive routing
Real-time behavior monitoring and adaptive routing Open API for seamless integration with SIEM, AI models, and analytics stacks
Open API for seamless integration with SIEM, AI models, and analytics stacks Visual dashboard with contextual traffic insights and anomaly alerts
Visual dashboard with contextual traffic insights and anomaly alerts
“How AI-Powered Proxies Optimize AI Infrastructure Costs — A Strategy Few Know”
#AIProxy #SmartProxy #ProxyAZ #EnterpriseSecurity #RealTimeProtection #DataPipelineSecurity #AIInfrastructure #CyberThreatDetection #NextGenProxy #MachineLearningOps #BigDataProtection #AIinBusiness #SIEMIntegration #ZeroTrustNetwork #SecureDataFlow #ProxySolutions #APISecurity #DDOSMitigation #AdaptiveRouting #DigitalTransformation

